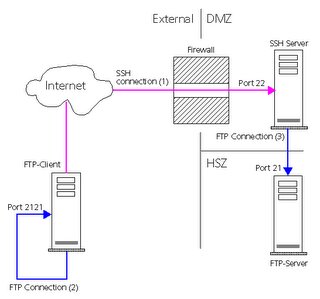
Rahul its for U .

Cisco CallManager server
Complete these steps in order to configure the Cisco CallManager server to automatically synchronize, and stay synchronized, with a Time server.
Note: You cannot use NTP to synchronize between two Cisco CallManagers. The NTP that is installed in Cisco CallManager is a client NTP service and only synchronizes to an NTP server.
1 file(s) copied.(NTP Operations Guide) in the C:\WINNT\..\xntp directory...Right-click on My Computer and select Manage.
Expand the Services and Applications section.
Select Services.
Double-click on the Network Time Protocol service.
Ensure that Start-up Type is set to Automatic.
Configure the C:\WINNT\system32\drivers\etc\ntp.conf file.
This file contains the list of Time Servers that Cisco CallManager becomes synchronized with. You can configure Cisco CallManager to point to specific Time Servers, or you can configure it to receive NTP broadcasts on the local LAN segment from the router (as long as the router is configured to do so).
Sample ntp.conf file that uses static Time Servers:
server patryk.keekar.com
server marc.keekar.com
driftfile %windir%\ntp.drift
Sample ntp.conf file that uses an NTP broadcast router:
broadcastclient
driftfile %windir%\ntp.drift
Go to the Services Control Panel and stop/start the NetworkTimeProtocol service. Allow several minutes for the update to take place.
Note: This procedure only applies to Cisco CallManager.
Complete these steps in order to install the NetworkTimeProtocol service:
Open a command prompt and change to this directory:
C:\>cd C:\Program Files\Cisco\Xntp
Run install.bat:
C:\Program Files\Cisco\Xntp>install.bat
Installing Configuration Files
1 file(s) copied.
Installing Executables
1 file(s) copied.
1 file(s) copied.
1 file(s) copied.
1 file(s) copied.
The NTP service is already installed
Remove it first if you need to re-install a new version
.
The NTP Service is now installed.
Please modify the NTP.CONF file in C:\WINNT appropriately.
.
See readme.txt for more information.
.
After modifying the configuration file, use the services control panel
to make NTP autostart and either reboot or manually start it.
When the system restarts, the NTP service will be running.
For more information on NTP Operations please see the NTPOG.Wri
C:\Program Files\Cisco\Xntp>
Note: This procedure only applies to Cisco CallManager.
Complete these steps in order to synchronize time manually with the Time Server using NTP.
Stop the NetworkTimeProtocol service in the Services Control Panel.
Synchronize the clock by using this commands from a command prompt:
In order to synchronize with a remote Time server:
ntpdate marc.keeker.com
Restart the NetworkTimeProtocol service in the Services Control Panel.
!--- Enable service timestamps datetime!--------------------------END --------------------------
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
!
!
!
!--- Hostnames for the MSFCs.
hostname MSFC15 alt hostname MSFC16
!
!
!
!Both MSFCs are in the PST timezone
clock timezone PST -8
!
!--- Both MSFCs will adjust the clock for Daylight Saving Time.
clock summer-time PDT recurring
!
!--- If connectivity to the NTP server is lost, the calendar is used.
!as an authoritative time source
clock calendar-valid
!
no ip finger
ip domain-name corp.com
ip name-server 172.16.55.120
ip name-server 171.16.60.120
!!
!--- Each MSFC uses the IP address of the loopback0 interface as
!--- the source IP for NTP packets.
ntp source Loopback0
!
!--- The MSFCs will update the hardware calendar with the NTP time.
ntp update-calendar
!
!--- Both MSFCs are getting the time from 10.100.100.1.
ntp server patryk.keekar.com
!
end
Configures SNTP to request NTP packets from an NTP server.
Router(config)# sntp server patryk.keekar.com [version number]
Configures SNTP to accept NTP packets from any NTP broadcast server.Router(config)# sntp broadcast client
Enter the sntp server command once for each NTP server. The NTP servers must be configured to respond to the SNTP messages from the router.
If you enter both the sntp server command and the sntp broadcast client command, the router will accept time from a broadcast server but prefer time from a configured server, assuming that the strata are equal. To display information about SNTP, use the show sntp EXEC command.
Content-switching and load-balancing vendors will add security functionality to their platforms, which already offer high-speed processing and deep packet inspection for making caching/load balancing type decisions. These vendors see security as a new revenue stream from their installed base, and as a way to avoid the threat of network security platform vendors that are adding switching and load-balancing functions to their platforms. Although content-switching/load-balancing vendors have extensive experience in wire-speed traffic processing, they don't have deep security expertise. This will prompt network performance vendors to acquire network security technology companies that specialize in deep packet processing.
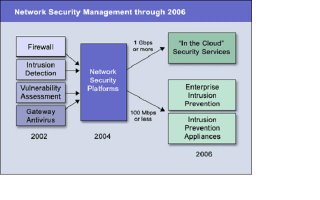
Network security platform market road map
In 2002, firewall vendors such as Check Point Software Technologies, Symantec, and NetScreen took steps toward becoming network security platform vendors. Check Point announced Smart Defense, which integrates intrusion detection capabilities onto Firewall-1. Symantec's Gateway Security product combines firewall, intrusion detection, gateway antivirus, and URL blocking functions into one appliance. NetScreen’s implementation of simple, signature-based filtering and its acquisition of OneSecure were strong moves in the platform direction.
However, these first-generation efforts provide minimal integration between functions, and they generally don’t add vulnerability assessment capabilities. Newer market entrants such as TippingPoint provide tighter integration of the required functions, but in a closed architecture that will require enterprise testing to determine the effectiveness of the individual firewall, intrusion detection, and antivirus functions, as well as integrated capabilities.
Gartner believes products that fully-integrated network security functions that can operate at wire speeds will not affect the firewall and intrusion detection markets until 2H04. After 2H04, intrusion detection vendors that do not offer network security platforms will begin to exit the market through acquisition by network security platform players or loss of market share.
The initial product focus between 2004 and 2006 will be at the enterprise level, with price points in the $25,000 to $75,000 range. If the telecom market recovers from the economic downturn before 2006, mainstream telecom and Internet service providers will begin to offer managed security services that will drive the development of higher-speed, lower-priced offerings and use-based pricing models. Gartner believes that aggressive telecom providers will offer some “in the cloud” services by late 2004. The low-end, small-and-midsize-enterprise-class network security platform will not be a market factor until 2007, when platforms with limited functionality and processing speeds will be available at price points of less than $10,000.
Managing multiple security devices
Most enterprises have deployed numerous firewalls, and many also have deployed one or more intrusion detection products. Network security platforms will be viable enterprise solutions by 2006, and they will transform today’s disparate network security market. Until that occurs, enterprises that have deployed firewalls and intrusion detection systems can use security device management products to gain a preliminary level of integration between network security products. These products support alarm/alert normalization, aggregation, data reduction and a degree of correlation to greatly reduce the false alarm rate and the operational burden of monitoring security devices. Although the loose integration that is provided by these products doesn't support the speed of response necessary to implement intrusion prevention, security management products enable enterprises to extend their investments in security products and provide a management structure for incorporating advanced security products.
Security management price points will have to drop below the six-figures of current offerings to reach the broad market. Outsourcing the monitoring and management of perimeter network security devices is another option for enterprises that are looking to avoid investing in early-stage technology or limited security staffing levels.
Bottom line
Tighter integration and common management across network security controls is a panacea of Internet security. Network security platforms maintain best-of-breed security approaches while supporting improved attack blocking and lowering total cost of ownership.
The probes are searching for systems that have vulnerable versions of LPRng, the "Next Generation" version of the widely used LPR printing utility, as well as the RPC daemon used with Network File System (NFS) services. While a large portion of these attacks were the result of U.S./Chinese cyberskirmishes following the downing of a U.S. spy plane, the subsequent hacking traffic has not died down. Check your software distribution's home page for an updated version of LPRng and RPC, and do so without delay!
Remember that automated probes are looking for TCP/IP listening ports that are associated with known system weaknesses. Make sure that you're running your Linux system with all ports disabled; save the ones that you absolutely need. In a terminal window, switch to superuser status, open /etc/inetd.conf, and comment out ports you're not using (for a single-user system that isn't functioning as a server, likely candidates include anonymous FTP, POP3, Telnet, rlogin, and rcp).
New vulnerability in wu-ftpd
I have recently found a article on net that vulnerability has been confirmed in the wu-ftpd FTP daemon. This vulnerability is remotely exploitable and can be used to execute arbitrary code on the vulnerable FTP server.
Because wu-ftpd is such a popular and widely used FTP server, not only for Linux but for other UNIX-derivatives like BSD systems, the security impact is quite high. The fact that most FTP servers in use these days provide anonymous FTP access compounds the problem. This means that a user doesn't even have to authenticate himself or herself on the server as a real user in order to exploit this vulnerability.
The problem is due to the "file globbing" support in wu-ftpd. This globbing allows clients to organize files for FTP actions, such as list and download, based on patterns. A heap corruption problem in the wu-ftpd, in its most innocent form, will simply cause the FTP server to die with a segfault. Unfortunately, this same corruption problem can be exploited to run programs on the server that the user should not be permitted to execute.
Most vendors have released updates to fix this problem quickly. Therefore, if you are running a version of wu-ftpd installed prior to Nov. 27, 2001, you are vulnerable and need to obtain an update from your vendor.Year 2005.
In future, if Prince Charles decides to re-marry . please warn the Pope!!
In last few weeks I attended lots of web cast and seminars regarding security. Also served different companies in different positions and roles. Its my observation companies are trying hard to protect their assets and get compliant so that they will not be target for hackers or so. Every one talks allot abt Network security , Application security , and so on . All those people talks abt big words like SQL injection , Buffer overflow, Format string vulnerabilities. But what these actually are and what precaution we have to take to get away from these is missing . I talked allot abt security with different vendors and finally found that only information which is coming to me is for Firewalls , IDS ; VPN , network audits , procedure audits and so . These things are essential but I was asking abt the complete security solutiuon no one highlited abt that we can also supress bugs related to these vulnaribilities at the time of devlopment too. Above aspects are most common and trust every guy working in security knows too. Hence net out come is that all vendors are trying to sell product not solutions.
Lots of well know bugs are present in already deployed software so ist essential to pretect them but what ever is going to be future please concentrate on that too. I worked with highly qualified test engineers they all talk abt the big testing software like Jtest, Robo J etc . But man where is mechanism which will tell u that the developers are generating an secure codes against the well know vulnerabilities. I know by this time this article seems boring to u . But this is the fact . Very few people know that their are automated tool present in market with the help of which you can suppress the mistakes already done earlier means vulnerability.
These automated tools do the audit on the principle of know mistakes or signature. For example if I am saying that buffer overflow vulnerability means their is improper usage of gets() , scanf(), sprint (), strcat (), strcp () function calls. Definitely these function call are required but some time by mistakes its not properly used which generate different kind of vulnerabilities. As per one survey their is 10000 + know vulnerabilities present and trust almost 50% of this figure is also analyzed by experts to know the patterns which commonly come to create vulnerabilities. So these automated audit tools match ur codes against these know patterns and if it find matching pattern of strings then it will give an alert for potential vulnerabilities. Some of the known audit tools are described below.
Automated Source Code Security Vulnerability Scanners
There are intelligent tools available to help you examine large amounts of source code for security vulnerabilities.
Flawfinder
Examines source code and reports possible security vulnerabilities
RATS from Secure Software Solutions
Scans C, C++, PERL, PHP and Python source code for potential security vulnerabilities.
ITS4 from Cigital
Scans source code looking for potentially vulnerable function calls and preforms source code analysis to determine the level of risk
PScan
A limited problem scanner for C source files
BOON
Buffer Overrun detectiON
MOPS
MOdelchecking Programs for Security properties
Cqual
A tool for adding type qualifiers to C
MC
Meta-Level Compilation
SLAM
Microsoft
ESC/Java
Extended Static Checking for Java
Splint
Secure Programming Lint
MOPED
A Model-Checker for Pushdown Systems
JCAVE
JavaCard Applet Verification Environment
The Boop Toolkit
Utilizes abstraction and refinement to determine the reachability of program points in a C program
Blast
Berkeley Lazy Abstraction Software Verification Tool
Uno
Simple tool for source code analysis
PMD
Scans Java source code and looks for potential problems
C++ Test
Unit testing and static analysis tool
Arena(known to self and others) bold, confident, extroverted, independent, knowledgeable | Blind Spot(known only to others) able, accepting, adaptable, brave, cheerful, clever, complex, dependable, dignified, energetic, friendly, giving, happy, helpful, idealistic, ingenious, intelligent, introverted, logical, loving, modest, nervous, observant, organised, patient, powerful, proud, quiet, reflective, relaxed, religious, responsive, searching, self-assertive, self-conscious, sensible, sentimental, silly, spontaneous, sympathetic, tense, trustworthy, warm, wise, witty |
Façade(known only to self)
| Unknown(known to nobody) calm, caring, kind, mature, shy |
able (15%) accepting (3%) adaptable (7%) bold (15%) brave (7%) calm (0%) caring (0%) cheerful (11%) clever (3%) complex (3%) confident (11%) dependable (15%) dignified (11%) energetic (3%) extroverted (11%) friendly (38%) giving (7%) happy (11%) helpful (11%) idealistic (7%) independent (11%) ingenious (3%) intelligent (38%) introverted (3%) kind (0%) knowledgeable (23%) logical (7%) loving (7%) mature (0%) modest (3%) nervous (15%) observant (15%) organised (11%) patient (3%) powerful (3%) proud (3%) quiet (15%) reflective (15%) relaxed (15%) religious (7%) responsive (3%) searching (7%) self-assertive (3%) self-conscious (11%) sensible (19%) sentimental (7%) shy (0%) silly (11%) spontaneous (7%) sympathetic (3%) tense (15%) trustworthy (11%) warm (7%) wise (7%) witty (15%)