What are network security platforms?
Network security platforms are network-attached devices that can apply multiple security functions (at a minimum, firewall, intrusion detection, and vulnerability scanning)at wire speeds. They provide environmental inputs (power, cooling and console) for the security capabilities, a common backplane for communications, and a structure for controlling communications between
security processing functions. Network security platforms use a variety of algorithms and techniques to inspect incoming and outgoing network traffic to determine if connections and payloads are dangerous to enterprises. The platforms decide whether to raise an alert regarding
suspected malicious activity or to take specific actions—such as blocking connections, dropping packets, or terminating sessions—when malicious activity is detected. These platforms perform functions that currently are performed by firewall network- and application-level), intrusion detection, vulnerability assessment, gateway antivirus, and URL blocking products.
Many network security platforms will include virtual private network capabilities; however, we believe that these capabilities will not be long-term platform requirements, except for site-to-site connections. Network security platforms must run at wire speeds; for most enterprises, these will be in the 100 Mbps to 1 Gbps range for single connections, and much higher for multiple networks. For “in the cloud” security applications, with which telecom and Internet service providers provide security processing in the network, throughput of 2 Gbps or higher will be required. These requirements will drive most network security platforms to be based on custom, application-specific, integrated circuits or network-security processors to support complex processing at high data rates. However, the platforms will need to support software-based updates, customization, and scripting similar to software-based systems. Hardware-based stack and protocol processing will be required to perform deep packet inspection without introducing unacceptable network latency.Software processing that runs on generic computing platforms will be sufficient where the network security platform primarily will be used for detection, not prevention; applications are simple or repetitive; or network data rates are low enough (see Figure ).
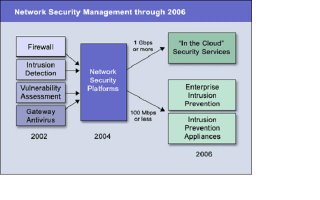
There are four primary types of network security platforms:
Closed integrated platforms—The network security platform vendor implements all security functions in a proprietary environment and can integrate processing across functions, which enables security functions to make processing decisions based on the results of other processing functions. Vendors in this category include Tipping Point Technologies, NetScreen Technologies, BlueCoat Systems, and Array Networks.
Closed separate platforms—The vendor implements all security functions in a proprietary environment without supporting integration across functions. Vendors include Symantec, with its initial Gateway Security product, and Cisco Systems, with its blade approach.
Open integrated platforms—The vendor licenses security functions from other vendors (or supports open source) or partners with multiple security vendors that port their applications to the network security platform. Vendors include Nortel/Alteon, CloudShield, and Ingrian Networks.
Open separate platforms—The vendor licenses security functions from other vendors (or supports open source) or partners with multiple security vendors that port their applications to the platform; however, integrated processing across functions isn’t supported. Vendors include Crossbeam Systems, Blade Fusion, and OmniCluster Technologies.
Closed integrated platforms offer more effective security via tighter integration between functions, but they require that enterprises abandon the best-of-breed approach to individual functions. Open integrated platforms enable enterprises to stay with best-of-breed options and preserve investments in network security products, as well as reduce the need to migrate security policies to new products.
Both types of separate platforms will be interim offerings until fully integrated capabilities are available. Meaningful integration across functions is a complex issue. Gartner believes that this integration will not provide reliable results until 2H04.
Within these types of platforms, different performance/price points will emerge:Carrier class—Products that run at OC24 and higher rates, and that allow network service providers to offer “in the cloud” security services, which eliminate the need for customer premises equipment and enable low-cost managed service offerings. Enterprise class—Platforms that can process multiple 100 Mbps networks that are used by Global 2000-class enterprises as enterprise intrusion prevention systems. Small and midsize enterprise class—Products that offer limited flexibility or operate at 100 Mbps or lower rates at low price points.
Content-switching and load-balancing vendors will add security functionality to their platforms, which already offer high-speed processing and deep packet inspection for making caching/load balancing type decisions. These vendors see security as a new revenue stream from their installed base, and as a way to avoid the threat of network security platform vendors that are adding switching and load-balancing functions to their platforms. Although content-switching/load-balancing vendors have extensive experience in wire-speed traffic processing, they don't have deep security expertise. This will prompt network performance vendors to acquire network security technology companies that specialize in deep packet processing.
Network security platform market road map
In 2002, firewall vendors such as Check Point Software Technologies, Symantec, and NetScreen took steps toward becoming network security platform vendors. Check Point announced Smart Defense, which integrates intrusion detection capabilities onto Firewall-1. Symantec's Gateway Security product combines firewall, intrusion detection, gateway antivirus, and URL blocking functions into one appliance. NetScreen’s implementation of simple, signature-based filtering and its acquisition of OneSecure were strong moves in the platform direction.
However, these first-generation efforts provide minimal integration between functions, and they generally don’t add vulnerability assessment capabilities. Newer market entrants such as TippingPoint provide tighter integration of the required functions, but in a closed architecture that will require enterprise testing to determine the effectiveness of the individual firewall, intrusion detection, and antivirus functions, as well as integrated capabilities.
Gartner believes products that fully-integrated network security functions that can operate at wire speeds will not affect the firewall and intrusion detection markets until 2H04. After 2H04, intrusion detection vendors that do not offer network security platforms will begin to exit the market through acquisition by network security platform players or loss of market share.
The initial product focus between 2004 and 2006 will be at the enterprise level, with price points in the $25,000 to $75,000 range. If the telecom market recovers from the economic downturn before 2006, mainstream telecom and Internet service providers will begin to offer managed security services that will drive the development of higher-speed, lower-priced offerings and use-based pricing models. Gartner believes that aggressive telecom providers will offer some “in the cloud” services by late 2004. The low-end, small-and-midsize-enterprise-class network security platform will not be a market factor until 2007, when platforms with limited functionality and processing speeds will be available at price points of less than $10,000.
Managing multiple security devices
Most enterprises have deployed numerous firewalls, and many also have deployed one or more intrusion detection products. Network security platforms will be viable enterprise solutions by 2006, and they will transform today’s disparate network security market. Until that occurs, enterprises that have deployed firewalls and intrusion detection systems can use security device management products to gain a preliminary level of integration between network security products. These products support alarm/alert normalization, aggregation, data reduction and a degree of correlation to greatly reduce the false alarm rate and the operational burden of monitoring security devices. Although the loose integration that is provided by these products doesn't support the speed of response necessary to implement intrusion prevention, security management products enable enterprises to extend their investments in security products and provide a management structure for incorporating advanced security products.
Security management price points will have to drop below the six-figures of current offerings to reach the broad market. Outsourcing the monitoring and management of perimeter network security devices is another option for enterprises that are looking to avoid investing in early-stage technology or limited security staffing levels.
Bottom line
Tighter integration and common management across network security controls is a panacea of Internet security. Network security platforms maintain best-of-breed security approaches while supporting improved attack blocking and lowering total cost of ownership.
1 comment:
Informative but from some other well known source .
Post a Comment